 nabble.documentfoundation.org
nabble.documentfoundation.org
Board Discuss - Proposal for Budget Process
http://nabble.documentfoundation.org/Proposal-for-Budget-Process-tp4154418p4156846.html
Document Foundation Mail Archive. Only in this topic. Proposal for Budget Process. Open this post in threaded view. Report Content as Inappropriate. Proposal for Budget Process. Having started to regularly publish our monthly ledgers, [1] and having. Published the grants page, [2] the next step is to have a regularly. Published, rolling budget, which is currently in the works. The board is. Currently working on optimizing the budgetting process, and here's a. Step 1: 3 Months. Reoccurring or One-Time Cost.
 erack.de
erack.de
erAck : GnuPG / PGP
http://www.erack.de/bookmarks/gnupg.html
Private mail being encrypted. My GnuPG public key. S fingerprint (and from the keyserver. BEGIN PGP SIGNED MESSAGE- - - Hash: SHA256 pub 4096R/0x6A6CD5B765632D3A 2013-01-10 Key fingerprint = 2265 D7F3 A7B0 95CC 3918 630B 6A6C D5B7 6563 2D3A - - -BEGIN PGP SIGNATURE- - - iQIcBAEBCAAGBQJUu/MgAAoJEGps1bdlYy06nAQP/1 FObMYbH74D8EjxYdcAHiL xq51FyjYg7E07m0yAbyGHB8rlytMRHbaQBe3vSy6YmkD4Oo95Kuda4qH4Nsra7Nu QoZfM0NwePk2wgUtPdJAyStUFoqBoEOAuokEsFWR8k2sdVLVygj8crD93nQ3uDDF F6uPsb28Khrpnzc5iI 8XZn679mcY9uJGHv4hrAyRJc...
 labs.gwendragon.de
labs.gwendragon.de
Domina de Ignis / GwenDragons technisches Blog
http://labs.gwendragon.de/blog
Sie sind in Kategorie Blogstart. Donnerstag, 25. August 2016. Vivaldi Final 1.3.551.38 – noch ein paar Bugfixes. Der Browser Vivaldi 1.3 Final hat ein Update auf Version 1.3.551.38 bekommen und so einige nervige Fehler aus der 1.3.551.30 gefixt. Vivaldi ist für die Betriebssysteme Linux, Mac und Windows in 32- und 64-bit-Versionen erhältlich. Changelog (seit 1.3.551.30). Regression] HTTP Status 302 opens an empty page VB-20337. Regression] Bookmark panel: Bookmark thumbnails not shown VB-19895. Mac] Unab...
 cryptologie.net
cryptologie.net
Cryptologie | Links
http://www.cryptologie.net/links
Here is a list of links I stumbled into and found interesting. Usually related to Crypto/Security although it could be anything. You can also suggest me something. Hyper-Threading and Multi-Core (2007). I'm going to tweet about interesting things I've found in the new NSA/Equation Group dump in this thread. Exploiting two buggy SRP implementations. NTRU and Lattice-Based Crypto: Past, Present, and Future. Good slides on chacha20-poly1305. Crypto and CHES 2016: 20 years of leakage, leakage, leakage.
 zwillingsstern.de
zwillingsstern.de
English | Zwillingssterns Weltenwald | 1w6
http://www.zwillingsstern.de/english/news
Thanks for all the fish. Mo, 10/31/2016 - 16:42 Draketo. AGU publications published "The world's biggest gamble", a short commentary on how to go on with climate change. Earth’s Future: The world's biggest gamble. Open Access: cc by). I am hard pressed not to become sarcastic. Not because the commentary is wrong. It’s spot on. But because we, as a species, are. Oh well, Happy Halloween and enjoy Samhain. Replacing man with info. Do, 10/13/2016 - 21:05 Draketo. Is lightyears ahead of. E G I sigh in the wi...
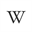 en.wikipedia.org
en.wikipedia.org
Public key fingerprint - Wikipedia, the free encyclopedia
https://en.wikipedia.org/wiki/Key_fingerprint
From Wikipedia, the free encyclopedia. Redirected from Key fingerprint. This article relies largely or entirely upon a single source. Relevant discussion may be found on the talk page. Please help improve this article. A public key fingerprint. Is a short sequence of bytes used to identify a longer public key. Fingerprints are created by applying a cryptographic hash function. Creating public key fingerprints. Using public key fingerprints for key authentication. Public key fingerprints in practice.
 sometimesicook.net
sometimesicook.net
Friends – Sometimes I Cook
https://sometimesicook.net/tag/friends
Burning Man Photo Diary. September 14, 2015. September 19, 2015. Experience. Every person there went to the desert with their own agenda and, to me, the essence of Burning Man is the acceptance of/ working toward every person’s unique burn. I met some incredible people there, listened to many wonderful stories, and came back a different (and I think better) human being. So I hope with the small bunch of pictures I took, I can convey even an ounce of the greatness that is Burning Man. August 10, 2015.
 sometimesicook.net
sometimesicook.net
California – Sometimes I Cook
https://sometimesicook.net/tag/california
Picnicking at Goat Rock Beach. August 5, 2015. September 19, 2015. For the awesome model of one of the boulders they made via drone. Share on Facebook (Opens in new window). Click to share on Twitter (Opens in new window). Click to share on Tumblr (Opens in new window). Click to share on Pinterest (Opens in new window). Click to share on Google (Opens in new window). Click to email (Opens in new window). Click to print (Opens in new window). Click to share on LinkedIn (Opens in new window). August 2, 2015.
 chasemp.github.io
chasemp.github.io
gpg getting started – devops type thoughts
http://chasemp.github.io/2015/04/29/gpg-getting-started
Wednesday, April 29, 2015 ». I am regenerating my GPG key. This is not my actual key shown ). Is an encryption standard. GNU PG (GPG) is a common implementation. GPG is. Used to transmit items securely, verify the integrity of source material, or to. Verify the identities of two parties. See reference for a download link and install a GPG implementation. Generating a key pair. Options: RSA/RSA, 4096, Valid for a year or more (this can be updated later). Key expires in n days. W = key expires in n weeks.
 sometimesicook.net
sometimesicook.net
Picnicking at Goat Rock Beach – Sometimes I Cook
https://sometimesicook.net/2015/08/05/picnicking-at-goat-rock-beach
Picnicking at Goat Rock Beach. August 5, 2015. September 19, 2015. For the awesome model of one of the boulders they made via drone. Share on Facebook (Opens in new window). Click to share on Twitter (Opens in new window). Click to share on Tumblr (Opens in new window). Click to share on Pinterest (Opens in new window). Click to share on Google (Opens in new window). Click to email (Opens in new window). Click to print (Opens in new window). Click to share on LinkedIn (Opens in new window). Sorry, your b...






